Email addresses have become a form of personal digital passport for identity resolution, essential for various online activities such as shopping (Amazon), payment transactions (Venmo), package security (UPS), subscription to newsletters, and social media engagement (Instagram, LinkedIn, TikTok). They also grant access to streaming services like Netflix, HBO, and Disney+.
With the addition of email encryption, and the core attributes of being persistent, unique, cross-device, and reliable, email addresses may be a gold mine for publishers and marketers.
So, how can publishers use this information while being mindful of privacy concerns? The answer: hashed email.
What is a Hashed Email?
Email hashing means turning email addresses into encrypted strings of characters. A hashed email becomes a unique 32, 40, or 64-character code, that appears as a jumble of random characters to the observer. A hashed email (HEM) is extremely difficult to decode without the special key used for encryption.
Hashing lets you use email addresses for targeting without revealing the actual email to partners or vendors. Your users' emails stay safe, and you get a unique code to create user profiles for better targeting.
How Do Hashed Emails Work?
Email hashing works by using a cryptographic algorithm to convert an email address into a fixed-length, seemingly random string of characters. Here's a simplified explanation of the process:
Input: The starting point is the email address that you want to hash (e.g., "example@getadmiral.com").
Hashing Algorithm: A hashing algorithm, like SHA-256 or MD5, is applied to the email address. This algorithm takes the input and processes it through a complex mathematical hashing function, producing a unique hash value. The same email address will always result in the same hash.
Fixed Length: The output hash is a fixed length, regardless of the length of the original email address. This makes the hash consistent and easier to work with.
Non-Reversible: One crucial feature of hashing is that it's a one-way process. You can't reverse the hash to retrieve the original email address. This property ensures that the email remains private.
Storage and Verification: The hashed email is then stored in a database. When a user provides their email for verification or login, the system hashes the provided email in the same way and compares it to the stored hash. If they match, access is granted.
HEMs are widely used in security and privacy applications to protect sensitive information while allowing for legitimate uses of email addresses, such as showing visitors targeted ads across devices.
Steps to Manage Privacy Concerns of Hashed Email
To use hashed emails to show targeted ads, publishers should update their privacy policies.
Include ways for users to opt-out and explain how hashed email info gets used. In the EU, consent management platforms must clearly say how this data gets used, giving users the power to make informed choices.
Here’s what publishers can do to address the privacy aspects of using HEMs:
Transparency: Be transparent with your visitors about data collection and use. Provide clear information about your data practices, including the use of HEMs for ad targeting.
User Control: Allow visitors to control their data. Offer opt-out mechanisms and give them the option to request the deletion of their hashed email from your databases.
Secure Data Storage: Safeguard the HEMs with strong security measures. Implement encryption, access controls, and regular security audits to protect against data breaches.
Obtain Explicit Consent: Publishers should obtain clear and informed consent from visitors before collecting or processing their email addresses, even in hashed form, for targeted advertising. Consent should be easily revocable.
Regular Audits: Conduct periodic privacy assessments and audits to ensure your data handling practices comply with privacy regulations and industry standards.
What are the Benefits of Hashed Emails for Publishers?
ID Solution in a Cookie-Less World: Adtech currently relies on third-party cookies to display targeted ads. However, once the third-party cookies are blocked on all platforms, hashed emails can be a great way to identify visitors for targeting across devices.
Precise Targeting: Email provides a precise and privacy-compliant method to reach your audience. Serve ads to those who have already shown interest and watch your RPM increase.
Cross-Channel Targeting: Emails link a user's devices (phone, computer, smartwatch, etc.), providing publishers with a comprehensive cross-device view of their interests.
5 Easy Ways Sites Can Collect Emails
Promote Newsletter Subscriptions: A preferred way for publishers to collect emails. This leads to an increase in traffic by re-engaging visitors and monetizing the newsletter through sponsorship and ads.
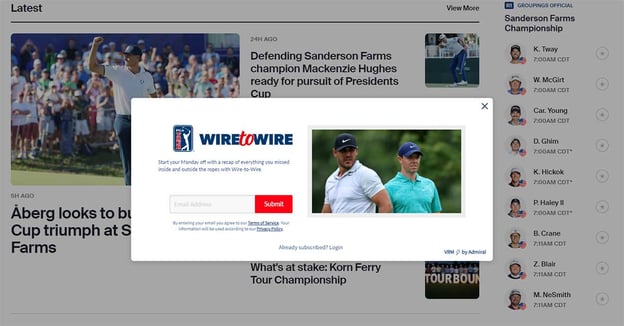 The PGA Tour is requesting visitors to subscribe to receive a recap email every Monday.
The PGA Tour is requesting visitors to subscribe to receive a recap email every Monday.
However, some publishers may not have the time and resources to start a newsletter. In such cases, the following options can help build an email list without the need to assemble a new team, and still provide revenue and retention value for the publisher.
Ad-free pass: Allow your visitors to experience your content without any ads for a few days in exchange for their email addresses.
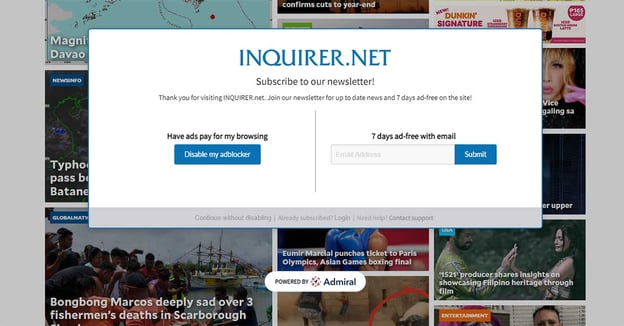 Inquirer offers a 7-day ad-free experience in exchange for an email address.
Inquirer offers a 7-day ad-free experience in exchange for an email address.
Set up a registration wall for visitors to authenticate: Registration walls are typically offered as a ‘free membership’ to site content or added benefits. They have been used by media publishers and e-commerce sites, such as Gilt, The Drum, New York Times, The Guardian, and Mediaite.
Admiral makes it easy by managing the user account, password, email, and support. Admiral can also help with customized CTAs and strategic advice based on working with thousands of sites. Regwalls are a great first step to tracking unique user journeys and growing consistent reader revenues.
To learn about the benefits, best practices, and examples of registration walls, visit this Registration Wall FAQ.

Paired with an adblock recovery solution: Target the audience using ad blockers; offer them an ad-free or ad-light experience in exchange for sharing their email address. It is a way for adamant adblock users to still support a site they value, which you can use to market to them for subscriptions and other products.

PremierGuitar is asking users to disable their ad blockers or, in exchange, offering a 30-day ad-free experience in return for their email.
In exchange for an offer: Ask your visitors to sign up with you and receive additional benefits such as coupons, deals, or access to premium content.
 VideoGamer offers credits to visitors for sharing their email addresses.
VideoGamer offers credits to visitors for sharing their email addresses.
Surge Targeting: Displaying custom messages to visitors on pages that are surging in traffic at that moment, or based on page popularity for the month. For example, you can ask visitors to sign up when they visit a page displaying scores from a live football match or a page with a breaking/viral news story.
Learn more about Surge Targeting here.
Publishers Should be Collecting Emails Now
Collecting emails is smart for publishers, and they should start now. It future-proofs your strategy, can contribute to more pageviews, retains your audience, and provides valuable insights.
Admiral offers easy-to-launch tools precisely to collect emails efficiently and has multiple strategies to fit your objectives. Get started in 24 hours with Admiral's one-tag solution.
Schedule a quick chat today.